
Kyverno: Kubernetes Native Policy Management
Pre-requisites
What is Kyverno?
Shortly Kyverno is a policy engine designed for Kubernetes. Policies can validate, mutate, generate, and cleanup Kubernetes resources, and verify image signatures and artifacts to help secure the software supply chain.
Lab (get your hands a little dirty)
Kyverno docs https://kyverno.io/docs/
Code is available on GitHub Link
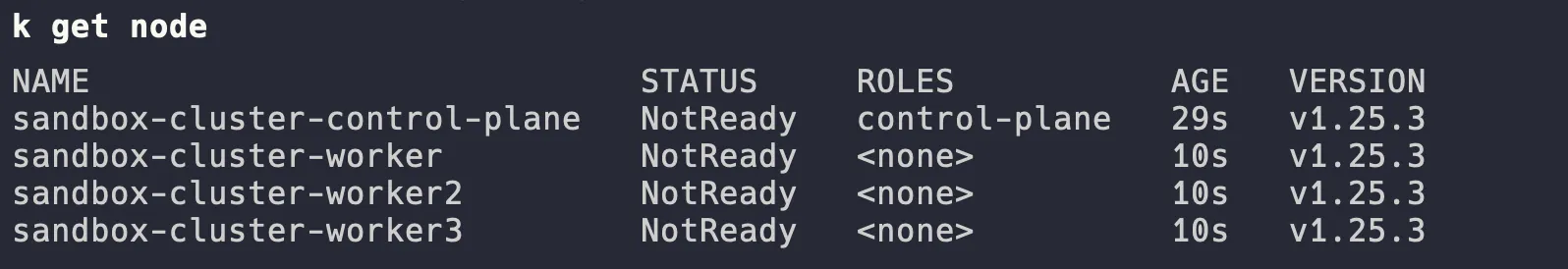
- Firstly, get your Kubernetes cluster up and running, I’m using Kind to do that. I am using Makefile to simplify the process. Clone repository and run the following command:
make create_clusterA sandbox Kubernetes cluster will be set up for you based on kind.yaml.
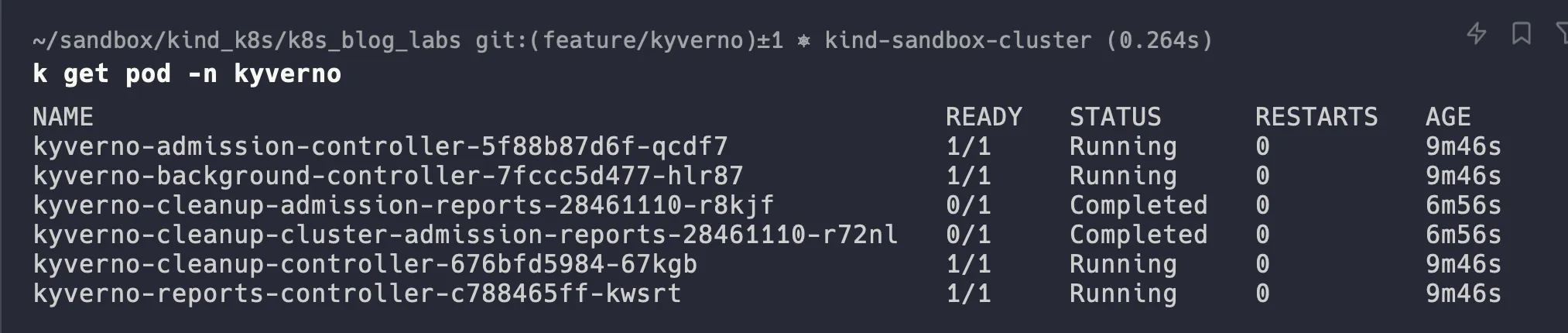
- Install Kyverno via helm chart
helm repo add kyverno https://kyverno.github.io/kyverno
helm repo update helm install kyverno kyverno/kyverno -n kyverno --create-namespace --set replicaCount=1 k get pod -n kyverno -wAfter installation you should observe:
- Check Custom Resource Definition
kubectl get crd | grep kyverno- Create a ClusterPolicy to enforce a label on all pods “policy_label.yaml” is in labs/kyverno directory
kubectl -f policy_label.yaml apply5.Test Cluster policy (creation ingress pod )
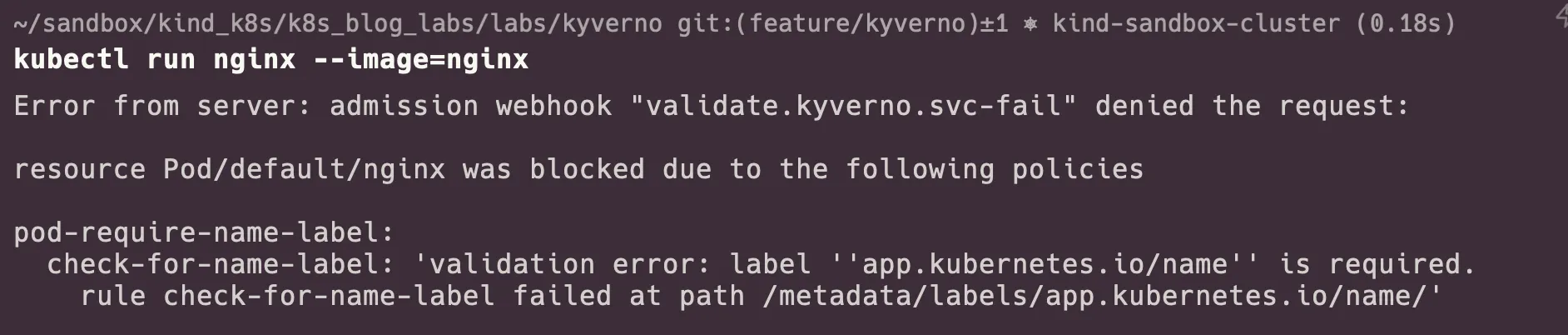
kubectl run nginx --image=nginxAs you can see the pod is not created because it does not have the label
It means that our Cluster Policy is working as expected
If you will add label to the pod it will be created
- At the end of this lab you can delete Kind k8s cluster.
make delete_clusterSummary
In this article, I showed you how to use Kyverno to enforce policies in Kubernetes. I hope you enjoyed this article and see you next time.